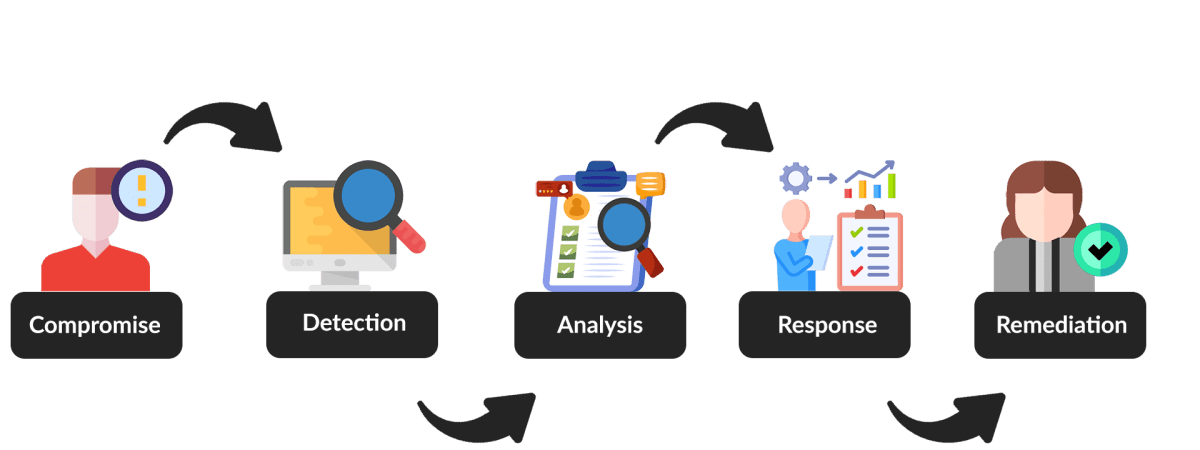
Managed Detection and Response (MDR)
Our Managed Detection and Response (MDR) service provides 24/7 surveillance of your digital assets, leveraging cutting-edge technology and expert analysis to detect, assess, and neutralize threats before they can impact your business
24•7•365 Continuous Monitoring
Utilize our team of expert forensic analysts, in any case available around the clock every day of the year, to carry out thorough investigations. Also, while benefiting from a comprehensive attack timeline based on meticulous endpoint forensic analysis, including scrutiny of artifacts like Master File Table records, Windows Event Logs, Registry entries, and Web History. During an incident response, our team provides essential threat neutralization assistance to mitigate and contain potential breaches.
Ongoing Expert Threat Hunting
A highly trained team of cybersecurity experts will continuously hunt through generated logs looking for anomalous and suspicious activity across your organization. Your environment will be baselined for known good behavior and we’ll alert you on deviations outside those recorded patterns.
Threat Intelligence Integrations
Harness the power of informed cybersecurity with our Threat Intelligence Integrations. This service synthesizes data from a myriad of reliable sources, providing your security systems with up-to-the-minute information on potential threats. By integrating this intelligence into your cybersecurity infrastructure, you’re not only strengthening your defenses but also enhancing your ability to predict and prepare for future attacks.

ONE UNIFIED PLATFORM FOR COMPLETE PROTECTION
Log Data Analysis
BastionX agents collect logs from operating systems and applications, securely transmitting them to the BastionX server for analysis and storage based on predefined rules. These rules help detect system or application errors, misconfigurations, malicious activities, policy breaches, and a range of other security and operational issues.
Vulnerability Detection
BastionX agents gather software inventory data and relay this information to the BastionX server. The server correlates the data with continuously updated CVE databases to pinpoint known vulnerabilities in software. This automated vulnerability detection enables you to identify and address security flaws in critical assets promptly, preventing potential exploitation by attackers.
Incident Response
BastionX offers built-in active responses for implementing countermeasures against ongoing threats. Triggered upon specific criteria, these responses may include blocking an endpoint’s network access from the source of the threat and other actions. BastionX can also execute remote commands or system queries, identify indicators of compromise (IOCs), and support incident response efforts.
Containers Security
BastionX provides security insights into Docker hosts and containers by monitoring their activity and identifying threats, vulnerabilities, and anomalies. With native integration into the Docker engine, BastionX users can oversee images, volumes, network configurations, and active containers. It continuously gathers and analyzes detailed runtime information. Not only alerting on containers operating in privileged mode, but applications with vulnerabilities, containers running a shell, changes to persistent volumes or images, and other potential security threats.
-
Configuration Assessment
BastionX ensures your system and application configurations comply with your security policies, standards, or hardening guides. It conducts regular scans through its agents to identify misconfigurations or security vulnerabilities in endpoints that attackers could exploit. Additionally, BastionX allows for the customization of these configuration checks, making them align precisely with your organization’s specific needs. Security alerts come with recommendations for improved configurations, relevant references, and compliance mapping.
Malware Detection
BastionX identifies malicious activities and indicators of compromise on endpoints, which may result from malware infections or cyberattacks. Its built-in ruleset and features, such as Security Configuration Assessment (SCA), Rootcheck, and File Integrity Monitoring (FIM), aid in detecting such activities and anomalies. These features of BastionX can be customized to fit your organization’s particular security requirements.
File Integrity Monitoring
BastionX monitors your file system for changes in content, permissions, ownership, and file attributes that are crucial to your operations. It also identifies the users and applications involved in the creation or modification of files. The File Integrity Monitoring capability of BastionX, combined with threat intelligence, helps pinpoint threats or compromised endpoints. Furthermore, FIM supports compliance with various regulatory standards, including PCI DSS, NIST, and more.
Thread Hunting
BastionX offers extensive visibility into your monitored endpoints and infrastructure, with features for log retention, indexing, and querying that assist in investigating threats that might have evaded initial security measures. Its threat detection rules are aligned with the MITRE ATT&CK framework, facilitating the investigation and identification of common attacker tactics, techniques, and procedures. BastionX also integrates with external threat intelligence feeds and platforms for superior threat-hunting capabilities.

